<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2018-08-30 11:58:33Computer security Prevention Security engineering Cyberwarfare Vulnerability Cryptography National security HackerOne Bug bounty program Information security Social vulnerability |
Add to Reading List |
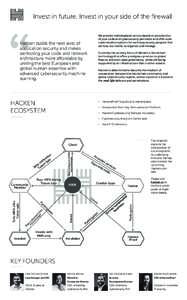
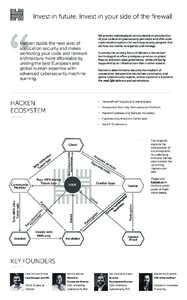
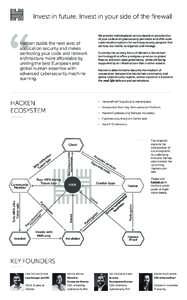
 What is a Vulnerability Disclosure Policy and Why You Need One VDPs work and they protect assets. That’s why the U.S. Department of Justice, the European Commission, and the U.S. Food & Drug Administration recommend th
What is a Vulnerability Disclosure Policy and Why You Need One VDPs work and they protect assets. That’s why the U.S. Department of Justice, the European Commission, and the U.S. Food & Drug Administration recommend th