11 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2005-02-08 17:18:01
|
|---|
12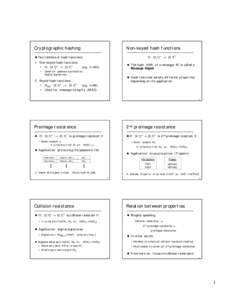 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2001-02-14 14:59:32
|
|---|
13![J. Cryptol[removed]: 588–613 DOI: [removed]s00145[removed]y Tweakable Block Ciphers Moses Liskov Computer Science Department, The College of William and Mary, Williamsburg, VA 23187, USA J. Cryptol[removed]: 588–613 DOI: [removed]s00145[removed]y Tweakable Block Ciphers Moses Liskov Computer Science Department, The College of William and Mary, Williamsburg, VA 23187, USA](https://www.pdfsearch.io/img/a90a74a6ab6e1e2b0fd7af7ae30aa282.jpg) | Add to Reading ListSource URL: www.cs.berkeley.eduLanguage: English - Date: 2015-01-21 19:48:40
|
|---|
14 | Add to Reading ListSource URL: www.iacr.orgLanguage: English - Date: 2006-04-18 10:40:57
|
|---|
15 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2014-09-11 11:03:47
|
|---|
16 | Add to Reading ListSource URL: www.slocounty.ca.govLanguage: English - Date: 2014-03-18 14:23:13
|
|---|
17![First Modes of Operation Workshop (October[removed]A Suggestion for Handling Arbitrary-Length Messages with the CBC MAC First Modes of Operation Workshop (October[removed]A Suggestion for Handling Arbitrary-Length Messages with the CBC MAC](https://www.pdfsearch.io/img/cee70523a6bb6243eea667d000736da0.jpg) | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2012-12-07 11:22:17
|
|---|
18 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2012-12-07 11:20:22
|
|---|
19![Second Modes of Operation Workshop (August[removed]PMAC: A Parallelizable Message Autentication Code Second Modes of Operation Workshop (August[removed]PMAC: A Parallelizable Message Autentication Code](https://www.pdfsearch.io/img/d51375d0473b7d53a94b8c4ac8cf8f2d.jpg) | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2012-12-07 13:10:47
|
|---|
20![First Modes of Operation Workshop (October[removed]Comments to NIST concerning AES Modes of Operation: PMAC: A Parallelizable Message Authentication Code First Modes of Operation Workshop (October[removed]Comments to NIST concerning AES Modes of Operation: PMAC: A Parallelizable Message Authentication Code](https://www.pdfsearch.io/img/7e2e0797715c6bfc0414fcd513068764.jpg) | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2012-12-07 12:41:02
|
|---|