<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2012-08-08 12:23:28Cryptography Keystream Applied mathematics Mathematics Initialization vector Block cipher modes of operation Block cipher Stream ciphers |
Add to Reading List |
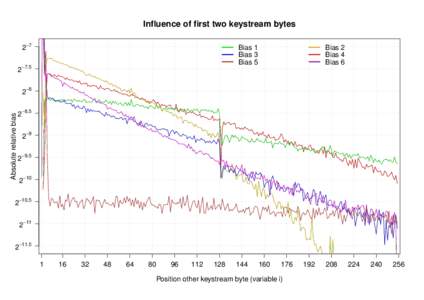 | Influence of first two keystream bytes 2−7 Bias 1 Bias 3 Bias 5DocID: 1xV86 - View Document |
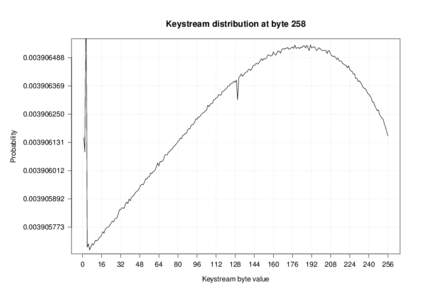 | Keystream distribution at byteDocID: 1xTZC - View Document |
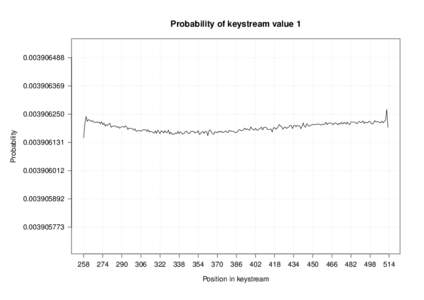 | Probability of keystream valueDocID: 1xTVG - View Document |
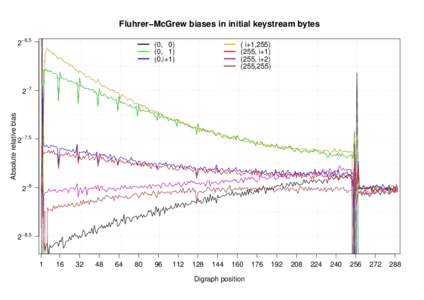 | Fluhrer−McGrew biases in initial keystream bytes 2−6.5 (0, 0) (0, 1) (0,i+1)DocID: 1xTHJ - View Document |
 | Biases in the RC4 keystream (128 bit uniform keys) Nadhem AlFardan and Dan Bernstein and Kenny Paterson and Bertram Poettering and Jacob Schuldt Royal Holloway, University of London University of Illinois at ChicagoDocID: 1tSaM - View Document |
 Block Cipher Modes of Operation-CCM Mode for Authentication and Confidentiality
Block Cipher Modes of Operation-CCM Mode for Authentication and Confidentiality