71 | Add to Reading ListSource URL: cups.cs.cmu.eduLanguage: English - Date: 2006-05-29 23:54:55
|
|---|
72 | Add to Reading ListSource URL: www.courts.state.nh.usLanguage: English - Date: 2016-07-21 09:33:18
|
|---|
73 | Add to Reading ListSource URL: dict.muhas.ac.tzLanguage: English - Date: 2013-06-28 01:32:44
|
|---|
74 | Add to Reading ListSource URL: www.trendmicro.comLanguage: English - Date: 2014-10-26 23:30:05
|
|---|
75 | Add to Reading ListSource URL: hotsoft.carleton.caLanguage: English - Date: 2015-06-02 08:51:22
|
|---|
76 | Add to Reading ListSource URL: texastuitionpromisefund.comLanguage: English - Date: 2015-09-01 00:02:56
|
|---|
77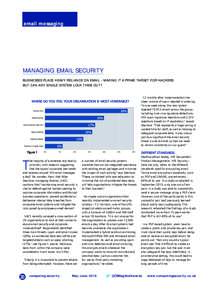 | Add to Reading ListSource URL: www.btc.co.ukLanguage: English - Date: 2016-05-16 06:54:47
|
|---|
78 | Add to Reading ListSource URL: www.voxuspr.comLanguage: English - Date: 2016-01-20 18:07:01
|
|---|
79 | Add to Reading ListSource URL: pages.phishlabs.comLanguage: English - Date: 2016-07-20 14:05:07
|
|---|
80 | Add to Reading ListSource URL: dmarc.orgLanguage: English - Date: 2015-09-16 19:35:07
|
|---|