41 | Add to Reading ListSource URL: www.brynmawr.eduLanguage: English - Date: 2014-08-21 12:58:35
|
|---|
42 | Add to Reading ListSource URL: mythreligion.philology.upatras.grLanguage: English - Date: 2012-08-28 08:07:24
|
|---|
43 | Add to Reading ListSource URL: pt.malwarebytes.comLanguage: English - Date: 2016-05-10 23:14:53
|
|---|
44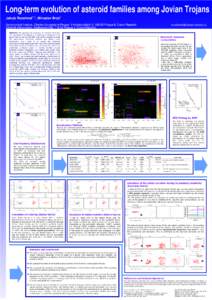 | Add to Reading ListSource URL: sirrah.troja.mff.cuni.czLanguage: English - Date: 2014-09-08 08:35:10
|
|---|
45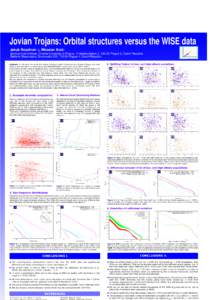 | Add to Reading ListSource URL: sirrah.troja.mff.cuni.czLanguage: English - Date: 2014-09-08 08:36:49
|
|---|
46 | Add to Reading ListSource URL: star.arm.ac.ukLanguage: English - Date: 2015-07-22 06:02:21
|
|---|
47 | Add to Reading ListSource URL: download.bitdefender.comLanguage: English - Date: 2016-02-24 10:16:54
|
|---|
48 | Add to Reading ListSource URL: www.cs.auckland.ac.nzLanguage: English - Date: 2009-03-30 21:48:24
|
|---|
49 | Add to Reading ListSource URL: conferenze.dei.polimi.itLanguage: English - Date: 2014-10-24 13:14:34
|
|---|
50 | Add to Reading ListSource URL: cryptome.orgLanguage: English - Date: 2015-09-04 06:14:52
|
|---|