<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Computing Information and communications technology Computer security Computer network security Data security Computer network Telecommunications engineering Firewall Trusted execution environment Transmission Control Protocol Packet forwarding Packet loss |
Add to Reading List |
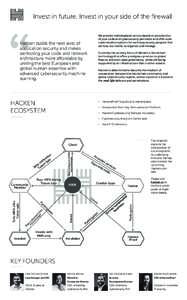
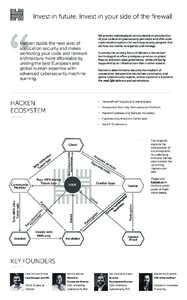
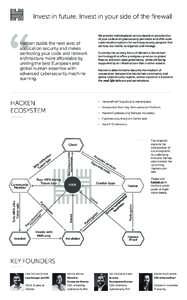
 Alcatraz: Data Exfiltration-Resilient Corporate Network Architecture Daniele E. Asoni ETH Z¨urich Email: Takayuki Sasaki
Alcatraz: Data Exfiltration-Resilient Corporate Network Architecture Daniele E. Asoni ETH Z¨urich Email: Takayuki Sasaki