1 | Add to Reading ListSource URL: www.idtheftcenter.org- Date: 2016-12-15 13:13:03
|
|---|
2 | Add to Reading ListSource URL: www.idtheftcenter.org- Date: 2016-12-13 18:27:51
|
|---|
3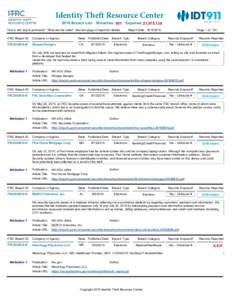 | Add to Reading ListSource URL: www.idtheftcenter.org- Date: 2016-08-16 19:59:21
|
|---|
4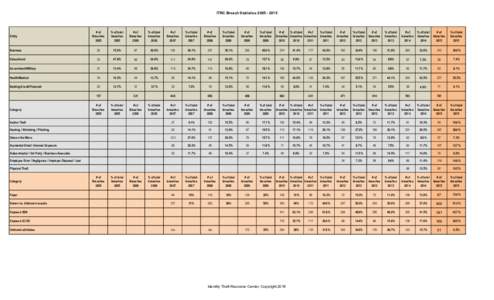 | Add to Reading ListSource URL: www.idtheftcenter.orgLanguage: English - Date: 2016-07-11 17:35:44
|
|---|
5 | Add to Reading ListSource URL: zoo.cs.yale.eduLanguage: English - Date: 2006-01-05 22:30:19
|
|---|
6 | Add to Reading ListSource URL: police.uci.eduLanguage: English - Date: 2015-09-03 20:35:20
|
|---|
7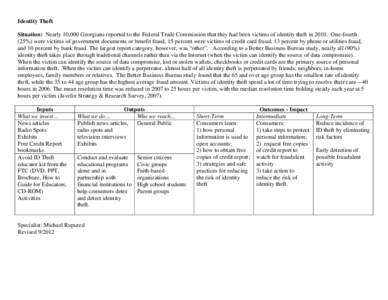 | Add to Reading ListSource URL: spock.fcs.uga.eduLanguage: English - Date: 2013-01-08 14:13:08
|
|---|
8 | Add to Reading ListSource URL: www.police.uci.eduLanguage: English - Date: 2015-09-03 20:35:20
|
|---|
9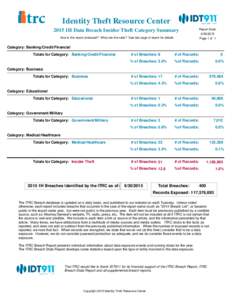 | Add to Reading ListSource URL: www.idtheftcenter.orgLanguage: English - Date: 2015-07-14 15:33:50
|
|---|
10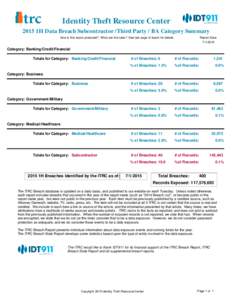 | Add to Reading ListSource URL: www.idtheftcenter.orgLanguage: English - Date: 2015-07-14 15:33:50
|
|---|